I’m a typical lurker. I don’t typically make an account on any given site, much less post. Thinking about it, though, many of the issues that I face are resolved through forum threads where someone actually went to the trouble of posting a question - usually a well-phrased, detailed question, but often something obtuse, or vague, or completely unrelated to the forum or subreddit they’re posting to, and yet points me in the right direction. Or whoever answered it put in far more work than whoever asked the question. I never know where I’m going to find a gem. It makes me feel that I should post, and maybe someone will find that relic someday and it be helpful to their own LAN journey.
All that said, I don’t see my lurk behavior changing any time soon (at least not until I implement an approach for email aliasing for junk accounts). I’m also dangerously close to getting philosophical.
But sometimes, when faced with an issue that I’m stumped on, I find it helpful to phrase a question as if I were going to post it to a forum like StackOverflow or SuperUser or r/networking.
I’m not feeling particularly inspired for this post, and I had already done a lot of prose-writing for this initial question - I went through this process a couple nights back. So, here is the question, as I would have asked it.
I will say, some of the question context was added after I figured this out, so it’s not completely organic. But the point of this exercise for me is largely thought distillation. Also, this question (more like questions plural, even) is probably way too long and detailed and incoherent to have induced any sort of cohesive answers.
OpenWRT as dummy WAP for two subnets - do I need to use VLANs?
tl;dr: I’m confused on swconfig vs dsa - where are lan1 lan2 etc? Why do I only see eth1.1 (Switch VLAN) as selectable bridge ports when creating a bridge device? Can I not separate the ports at the interface level, without the use of VLANs?
Relevant links:
- https://openwrt.org/docs/guide-user/network/dsa/dsa-mini-tutorial
- https://openwrt.org/docs/techref/swconfig
My actual question with (maybe too much) context:
I’ve been wanting to set up a guest WLAN, totally isolated, for some time now, but I’m just now to the point in the setup where I have my two-port router connected to a managed, VLAN capable switch.
My physical setup is as follows:
- OPNsense router-on-a-stick (Protecli Vault V1211)
- Managed switch with VLANs properly configured (Cisco CBS350-16T-2G)
- Dummy WAP (Netgear Nighthawk X4S R7800) running OpenWrt Netgear Nighthawk X4S R7800
My VLAN/subnet setup is as follows:
- User network: VLAN 10, subnet
10.0.10.0/24(WAP on this subnet) - Guest network: VLAN 40, subnet
10.0.40.0/24(I want my WAP to also be on this subnet)
Until this point, I’ve just used myOpenWrt router as a dumb WAP (mostly according to thisguide) and left all my LAN in one subnet. The two important VLANs/subnets are listed above, and they are working (meaning DHCP, internet access, and routing properly between subnets - no firewall rules in place yet.)
I’ve basically neutered the entire routing and firewall functionality of the Wrt device, on purpose. I let all traffic pass back to the OPNsense router/firewall. This dummy WAP has been working for months now, and the VLAN separation I implemented a week ago hasn’t run into any real issues.
But as for implementing the guest network, I’m stumped. I don’t want to have to break out another WAP, I am certain that I can use this one and run two networks. My theory is that I should be able to create two separate devices based on two separate physical LAN interfaces on the WAP, and plug them into two separate ports on my switch. Then, just create the interfaces, attach them to the wireless radios, and off to the races.
The problem I’m running into is the fact that the only ports available to select on the device creation screen (Network → Interfaces → Devices) are Switch VLAN ports, not lan1 lan2 etc like I have seen in DSA configuration. Apparently I am not running DSA. So my question is: is there any way to reference the ports as separate entities, or add them as network devices, under swconfig? Or do I have to utilize VLANs? (Not that I have any inherent problem with VLANs, I have simply preferred to turn off features on the WAP that I do not need, so as not to introduce any unnecessary complication to the network. All layer 3 functionality should be handled by the OPNsense router.)
Other questions that may be related:
- WTH are the
eth0andeth1interfaces? I was reading something to do with passing traffic to the CPU but I’ll be honest I did not understand it. Does one or both of those need to be tagged, if using VLANs? - Could I do this with one cable, with some sort of VLAN configuration that I am not understanding?
Note
This next part of the question was by all means unnecessary, but I liked what I wrote here, especially for the purpose of having it in this blog post instead. So I am leaving it.
I apologize in advance that I am not well-versed in UCI / the OpenWrt config files. It’s a shortcoming of mine. I generally dislike configuring via GUI but I haven’t had the wherewithal to dive into CLI configuration for these devices - my intention has been to move away from consumer-grade networking equipment, and while I appreciate the OpenWrt project, it’s quite limited for my needs (and honestly obtuse) - which I can understand, developing this software for so many shitty consumer-grade routers is a herculean effort in itself, and my hat is off to their team. I’m complaining, but it was my first step into configuring my home LAN, and GOD it is so much better than the shit ISPs put on their routers.
Working configuration
Overview
Some helpful links:
The ultimate answer to my non-posted question was simply to use VLANs in lieu of device/interface separation of the ports.
- VLANs should be enabled on WAP.
- Two separate cables should be running from WAP to switch.
- 5gHz radio will be running primary WLAN.
- 2.4gHz radio will be running guest WLAN (turned off unless I have someone over).
Physical
- LAN port 1 on the WAP connected to switch, VLAN 10 access port
- LAN port 2 on the WAP connected to switch, VLAN 40 access port
WAP
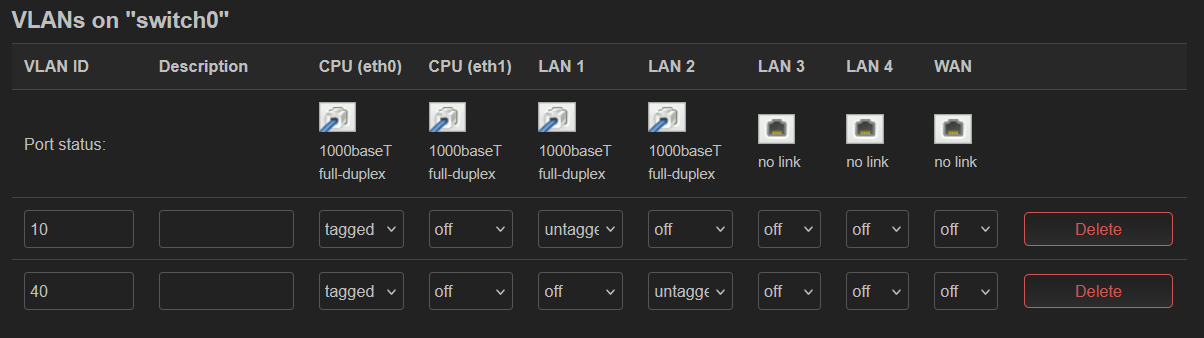
Network → Switch
- Check “Enable VLAN functionality” if unchecked
- Create two VLANs, id 10 and id 40
- eth0 tagged on both (eth1 off on both, if present - this confused me)
- lan1 untagged on 10
- lan2 untagged on 40
- lan3, lan4, and wan OFF on both
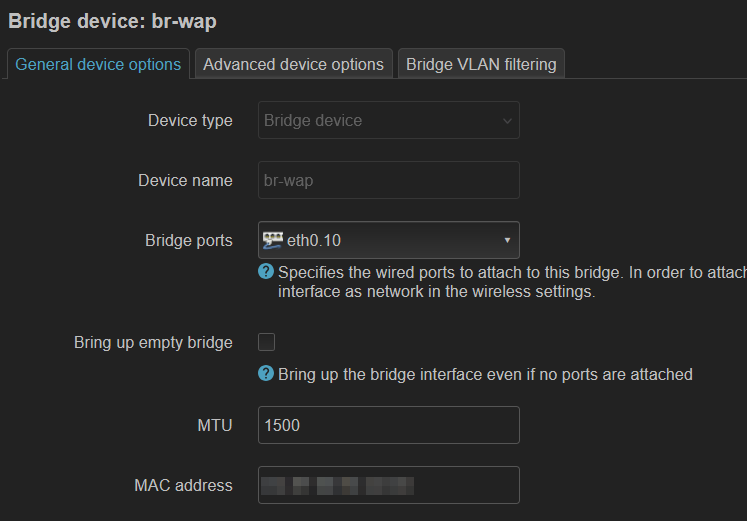
Network → Interfaces → Devices
- Add device
- Device type: Bridge device
- Name: “br-wap”
- Bridge ports: eth0.10
- Add device
- Device type: Bridge device
- Name: “br-guest”
- Bridge ports: eth0.40
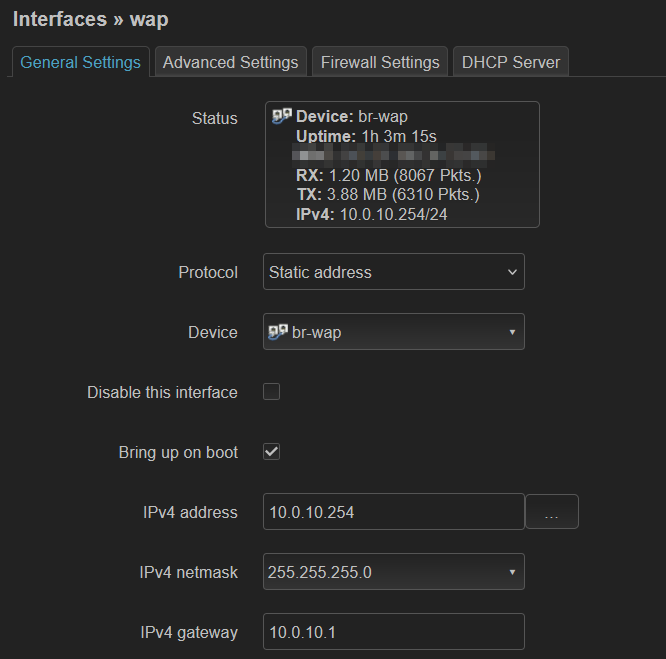
Network → Interfaces → Interfaces
- Add new interface
- Name: wap
- Protocol: static address
- Device: br-wap
- IPv4 address:
10.0.10.254 - IPv4 netmask:
255.255.255.0 - IPv4 gateway:
10.0.10.1
- Add new interface
- Name: guest
- Protocol: static address
- Device: br-guest
- IPv4 address:
10.0.40.254 - IPv4 netmask:
255.255.255.0 - IPv4 gateway:
10.0.40.1
Network → Wireless
Add a new wireless network to radio1, using the guest interface. You’ll give it an SSID and set up security + password. Also good measure to tick the box to isolate client communication under the Advanced Settings tab when doing this.
Note
Reviewing this, it is possible to add multiple SSIDs to a single radio…this could be useful! I will have to investigate this option more.
If doing this from scratch
How I neutered the WAP. This configuration was already present. I detailed it here.
- No routes should be present in the routing table
- All firewall zones should be deleted
- Input, output, and forward should all be set to accept
- All Port forwards, Traffic rules, and NAT rules should be empty
- DHCP and DNS should be fully disabled
OPNsense
My suggestion is to create an alias for all the other VLANs/subnets - since there are so many of them, you can create one firewall rule instead of a new rule every time you add a VLAN. Note that you WILL need to update the alias every time you create a new VLAN interface - but you won’t have to create a new firewall rule on every single relevant interface.
Conceptual rules:
- Default auto-generated
- Explicit pass for DNS
- Explicit block for firewall access
- Explicit block for other VLAN/subnet access
- Default allow at the end of the chain
Firewall rules should look like the following:
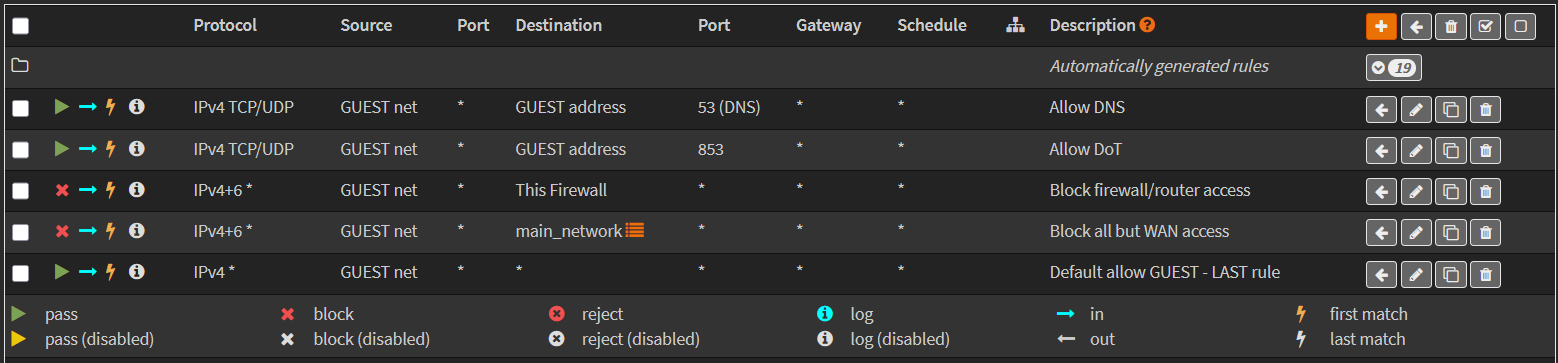
Note that for my use case I had to use port 853 for DNS over TLS, since I have that configured as the default in place of normal port 53 DNS.
Wrap-up
This bodes well for the rest of my LAN separation via VLANs, which I am working on mapping out before I jump into the rest of it. This was my first real crack at firewall rules.
Key developments (in my head) include an isolated-from-WAN network for devices (like printers) that I would like to access over the LAN, but in no world need internet access, and a totally isolated WLAN (for stuff like game consoles) that in no world need access to my LAN, but need to connect to the WAN. (The guest network as it stands would suffice for this, but that’s not really what it’s for.)
I get the feeling I’m gonna need more wireless access points…but if the discovery that I can host more than one interface device on each radio works, then I can have up to 4 on this router (5 if I can figure out how to utilize the WAN port as a LAN port).
EOF